Nerve's modules and their features
Base Features
Nerve offers a set of base features. These features provide a secure foundation for managing software and devices on our IIoT platform Nerve.
The Nerve Management System provides a central point for managing all connected edges. Users update the Service OS, monitor performance and deploy and manage workloads. It is available as a hosted service run by TTTech Industrial, or for on-premise (or on customer cloud) installation.
The hypervisor's hardware-based separation provides perfect isolation for real-time performance, reduces complexity and significantly increases run-time security.
Nerve DNA, short for Deterministic Node Automation, is a mechanism for simplifying edge commissioning and scaling roll-out agendas. Using a declarative approach to configuration, the user can list all applications and configuration definitions in a DNA file. The DNA file is sent to the edge devices for application.
Nerve incorporates a wealth of features to ensure that the system is always secure and that production data is protected. All connections are secured with TLS. Nerve is regularly penetration tested. Software processes comply with IEC62443 4-1.
Nerve Nodes provide full functionality even if, for whatever reason, they are disconnected from the Management System. When a Node comes online, the Management System synchronizes with the Node and recognizes any changes made while it was disconnected.
Nerve can be managed through an API for automating repetitive tasks or for connecting the Nerve Management System to other systems.
All system events, audit logs, edge events and applications are logged centrally. Pre-configured dashboards allow users to get started quickly.
Nerve Edge SW can run on any IPC. For guaranteed real-time performance a device qualification service is available. Nerve without real-time capabilities can be used as VM in virtualized environments.
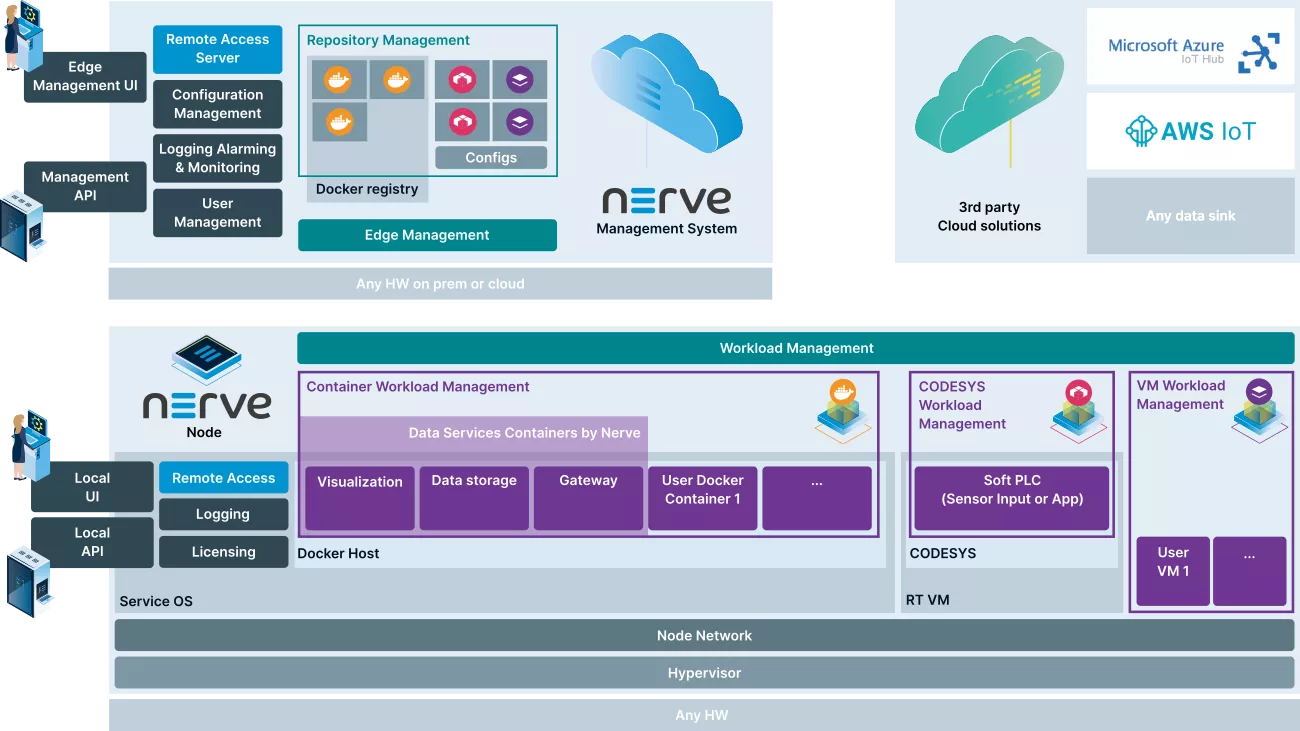
Edge Hosting
The Edge Hosting feature enables you to run multiple applications in the form of e.g. Docker containers and virtual machines side-by-side on standard industrial hardware and manage them locally or remotely from cloud.
Docker container management
- Nerve Edge can run standard Docker containers. Docker images are securely stored in Nerve's Management Systems registry for distribution to the Edges. Nerve allows to apply persistent configuration files that include specific settings.
Virtual machine management
- Nerve Edge can run virtual machines in its hypervisor. Applications and operating systems can be migrated from existing solutions into Nerve.
CODESYS Applications - 61131-3
- Nerve Edge supports CODESYS 61131-3 PLC applications as workloads. 61131-3 PLC applications can be programmed and tested using the CODESYS IDE.
The workload repository in Nerve's Management System holds all applications and their configuration. Workloads are applications with additional parameters needed for their installation and runtime Edges get workloads only from the central repository to ensure security and manageability.
Secure roll out agendas can be driven with the Nerve Management system. Roll outs can include all Nerve Edges worldwide or target only individual Edges. Service personnel can immediately use the Edge after roll-out.
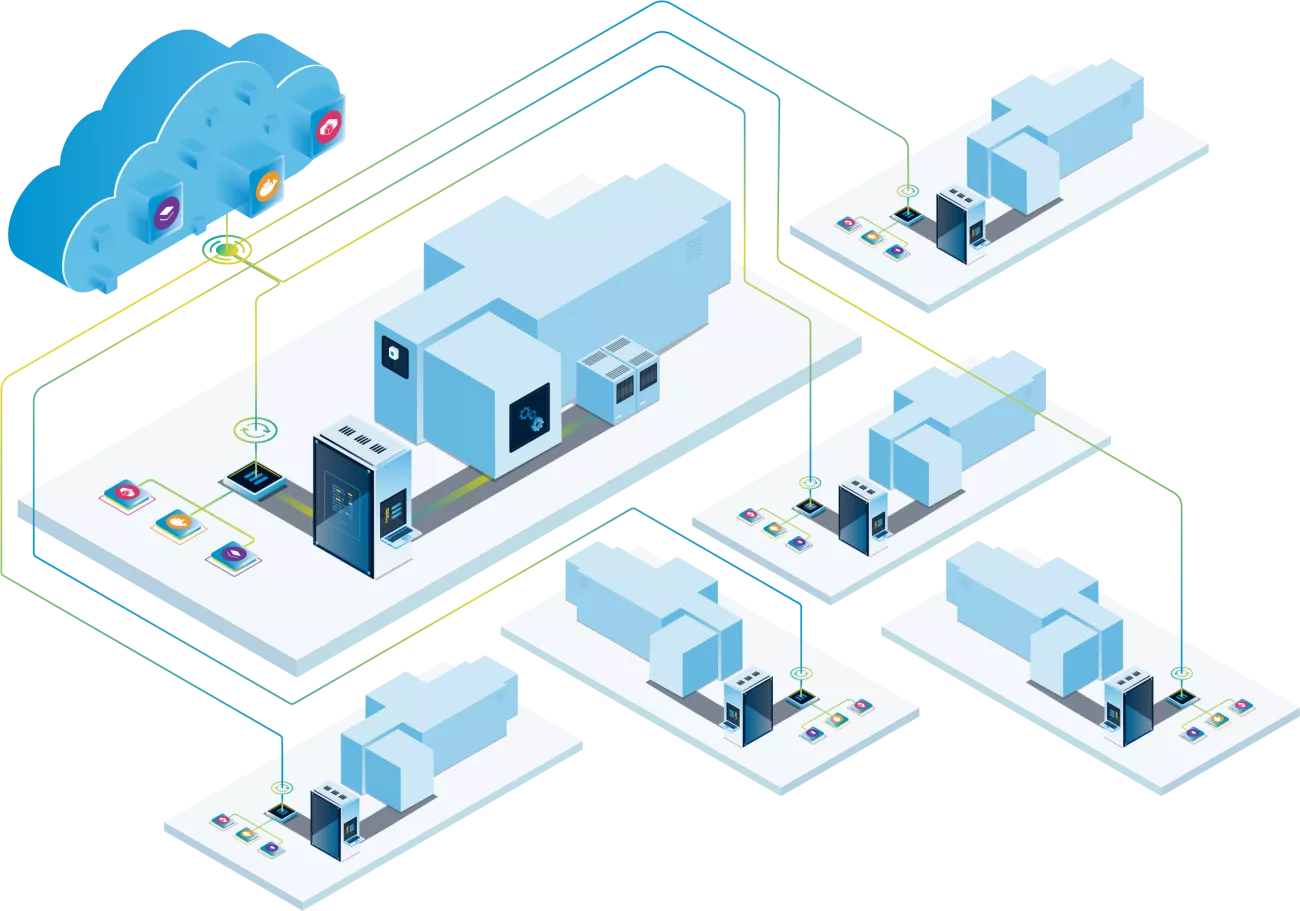
Central workload repository - Cloud or on-premises
Secure rollout agendas across multiple Nerve Edges can be managed with the cloud-based Nerve Management System.
Edge Hosting allows multiple applications to run side by side.
CODESYS Application - 61131-3
Docker containers
Virtual Machines
The Nerve Edge software runs on standard industrial hardware
Data Services
The Data Services feature helps you create real-world IoT use cases, providing analytics, modern dashboards and seamless data transfer between sensors and the cloud. Whether you are retrieving sensor data, connecting to a PLC, storing, and visualizing data, or sending data to third-party cloud services, Data Services simplifies the process.
The Nerve Data Gateway can be configured to read data from multiple sources and forward it to deployed applications or clouds. It is configurable for multiple sources and destinations. The data gateway is optimized for high performance, enabling fast cycle times down to 1ms. It is graphically configurable for ease of use.
The Data Gateway also includes advanced OPC UA server and client functionality. Both server and client support encryption and authentication using certificates or username/password.
The Data Gateway supports MQTT as an input and output protocol, again with certificate and username/password based security features. Data is formatted in JSON and includes accurate timestamp information.
For high performance data exchange between applications and the analytics applications, the Data Gateway allows the use of ZeroMQ.
The Data Gateway can send data directly to third-party clouds, such as the Microsoft Azure IoT Hub, giving you a head start on your applications on Microsoft Azure.
Nerve has built-in visualisation for data at the edge. For this purpose, an unmodified Grafana system is integrated. It uses the built-in databases as data sources.
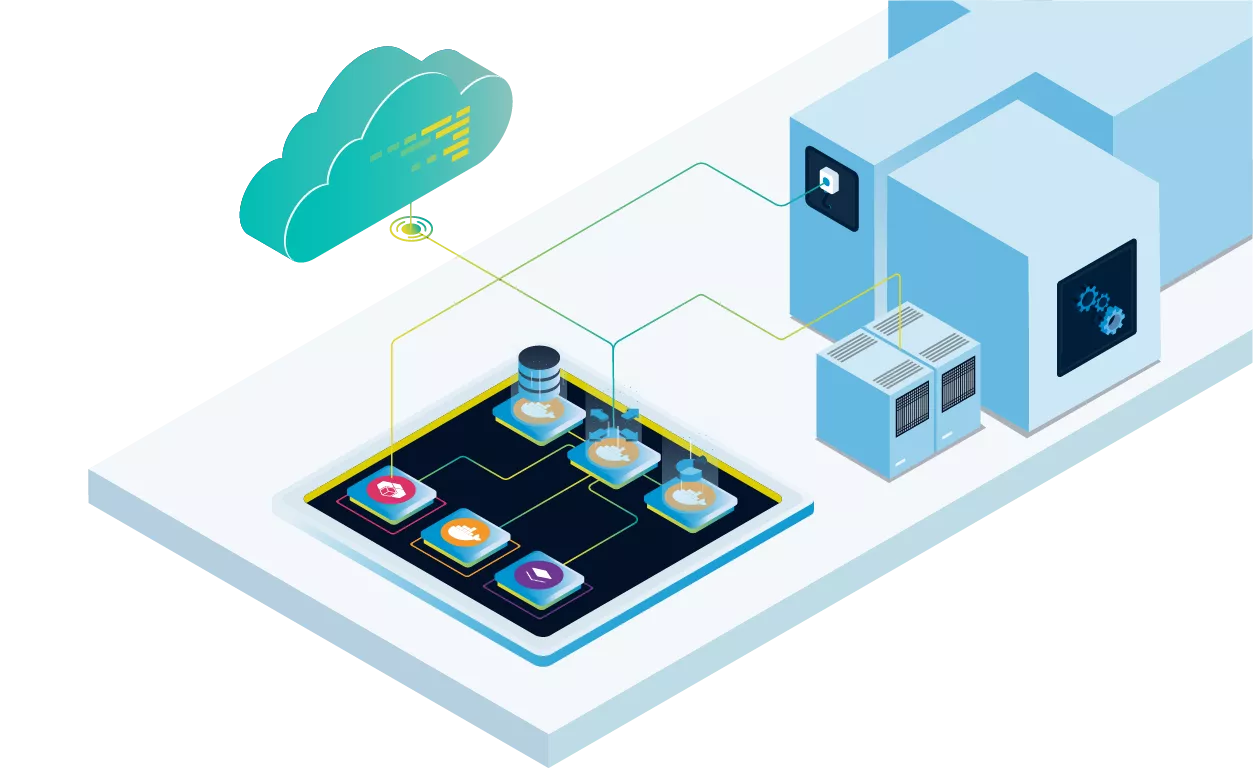
Built-in data connector to 3rd party clouds e.g. Azure IoT connector
Get Data from Fieldbus Sensors, e.g. EtherCAT or PROFINET
Database
Multi-protocol Data Gateway (OPC UA, S7, MQTT, etc.)
Integrated data visualization in dashboards
Connect to a PLC and collect data e.g. via OPC UA
Remote Services
The Remote Services feature allows you to remotely connect to workloads and devices in the field. Nerve becomes a secure hub (jump host) for remote access to any device on the machine or production network.
You can connect to services running in workloads, the CODESYS runtime running on the Edge, or the Service OS of the Edge itself. Remote tunneling can be used to connect to, for example, a web-based user interface (UI), a command line or a FTP server.
The tunnelling mechanism can also be used to access and configure devices in an edge's network. For example, engineering tools can access the local OPC UA Server.
Nerve gives you remote access to workload screens and shells right in your browser. This also allows you to observe the boot and shutdown process of a workload.
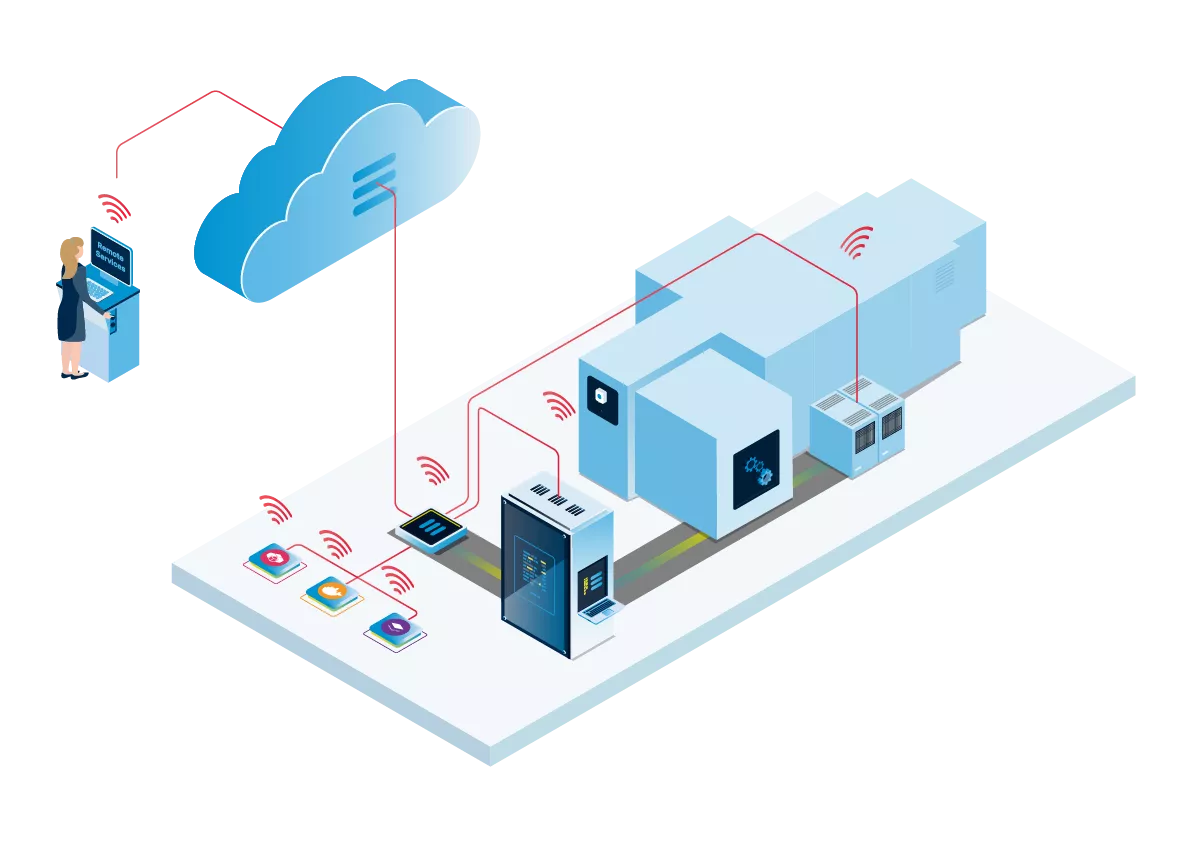
Remote Connections can be initiated by any PC with the Nerve Remote Connection Software
Remote connections are always securely executed by the Management System
Remote connection to the Local Management UI of the Nerve Edge
Remote connection to deployed applications of the edge for example to a web-based user interface (UI), screen, shell a command line, or an FTP server
Remote connection to the Service OS of the Edge itself
Accessing external devices
The tunnelling mechanism can also be used to access and configure devices in an edge's network. For example, engineering tools can access the local S7 or OPC UA Server.
Soft PLC
The Soft PLC module can be used to run machine control workloads on standard IPC hardware and access sensors and actuators through fieldbus Remote-IO.
Nerve integrates the CODESYS runtime inside a real-time VM. CODESYS applications are written in 61131-3. The runtime can be reached with Remote Services and the CODESYS 61131-3 PLC applications can be distributed to nodes via the Nerve Management System and are fully managed.
The Soft PLC supports multiple fieldbus protocols. It can act as an EtherCAT master, Modbus Master, PROFINET master and PROFINET device. Nerve supports a dedicated, high speed network port for the fieldbus connections to CODESYS.
The CODESYS Soft PLC runs down to 1 ms cycle time, taking advantage of the computational power of Intel CPUs.
The CODESYS Soft PLC includes retain variable support. Nerve provides a library to help users with this feature.
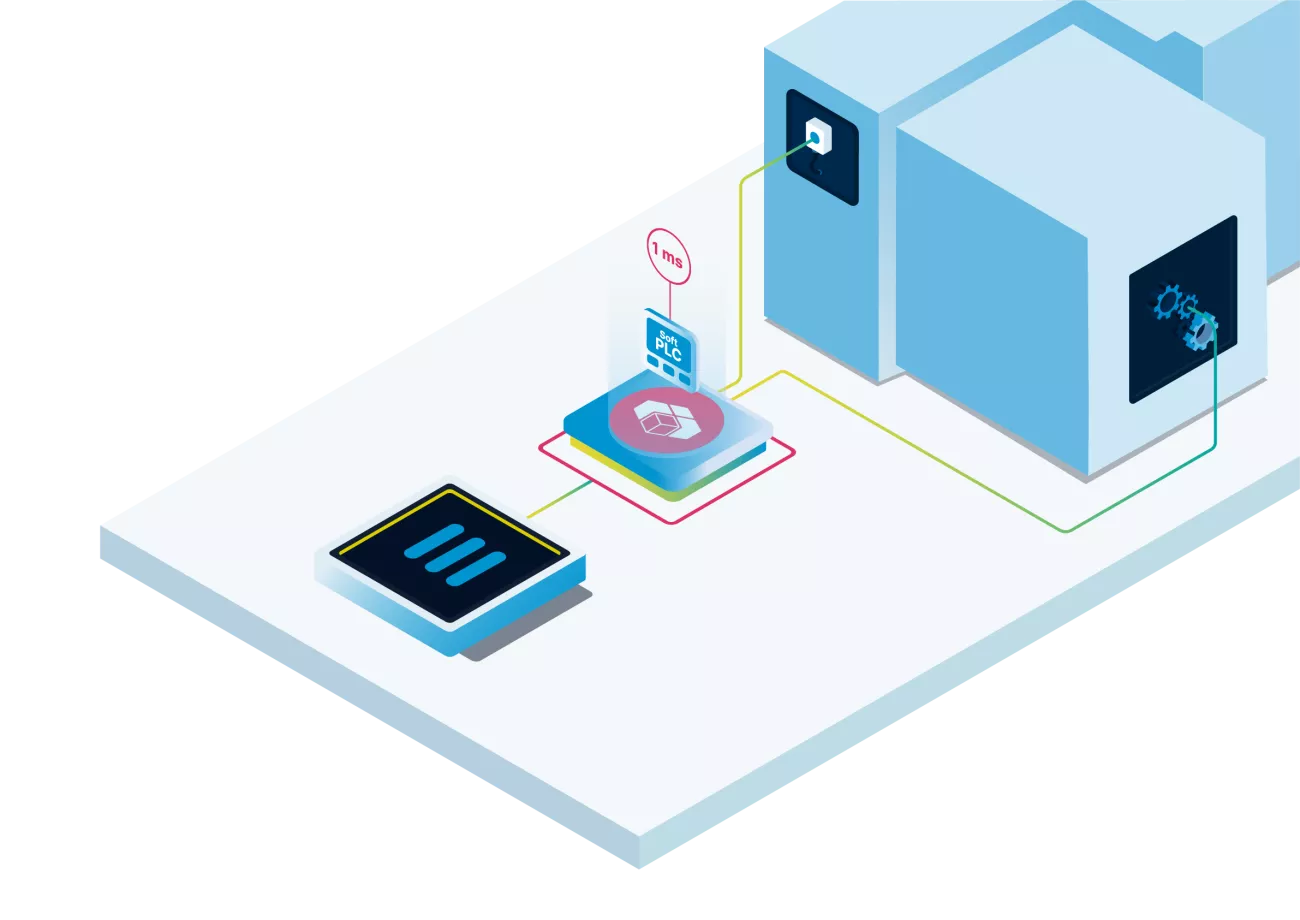
Fieldbus connectivity to sensors e.g. PROFINET, EtherCAT
Fieldbus connectivity to actuators e.g. PROFINET, EtherCAT
The CODESYS Soft PLC runs down to 1ms cycle time, taking advantage of the computational power of Intel CPUs
Nerve integrates the CODESYS runtime inside a real-time VM. The CODESYS 61131-3 PLC applications can be distributed to nodes via the Nerve Management System and are fully managed.

